 Scientists at the Griffith University in Queensland claim quantum physics will help protect data on the internet.
Scientists at the Griffith University in Queensland claim quantum physics will help protect data on the internet.
 Scientists at the Griffith University in Queensland claim quantum physics will help protect data on the internet.
Scientists at the Griffith University in Queensland claim quantum physics will help protect data on the internet.
 A number of official Gernan government sites have been hacked by a group that claims affinity with the Russian government’s moves in Ukraine.
A number of official Gernan government sites have been hacked by a group that claims affinity with the Russian government’s moves in Ukraine.
 A former news writer at CBS has started a law suit, accusing the US Justice Department of illegally hacking into her computers.
A former news writer at CBS has started a law suit, accusing the US Justice Department of illegally hacking into her computers.
 A German hacker said he cloned the thumb print of defence minister Ursula von der Leyen using little more than an ordinary digital camera.
A German hacker said he cloned the thumb print of defence minister Ursula von der Leyen using little more than an ordinary digital camera.
The BBC said Jan Krissler grabbed several photographs of von der Leyen’s thumb at different angles during a press conference last October.
Although fingerprint recognition is not considered particularly secure, some vendors use them to access devices.
Back in the 2000s, some Japanese banks adopted fingerprints as a chief biometric to access ATMs, but abandoned them after gangsters demonstrated that one way to circumvent security was to chop off peoples’ index fingers and use them to get money from the hole in the wall.
Companies are experimenting with other biometrics such as vein recognition and iris recognition.
 North Korea’s only ally, mainland China, has condemned the hacks on Sony but said there is no proof it was behind the attacks on the movie company.
North Korea’s only ally, mainland China, has condemned the hacks on Sony but said there is no proof it was behind the attacks on the movie company.
A report in Reuters quoted a spokesperson as saying that while China was against any cyberattacks and cyber terrorism, there is no proof that North Korea was the culprit.
North Korea claims that it had no idea which individual or group had hacked Sony Pictures but its press agency said “we can surely say that they are supporters and sympathisers with the DPRK”.
It threatened action against the US which it described as “the cesspool of terrorism”. US president Obama said his country would take action against the perpetrators of the hack, but did not specify what such action would be.
In a statement, the official North Korea news agency said the USA should “honestly apologise to makind for its evil doing”.
North Korea “highly estimates the righteous action taken by the guardians of peace, though it is not aware of their residence”.
It continued: “The army and people of the DPRK who aspire after justice and truth and value conscience have hundreds of millions of supporters and sympathizers, known or unknown, who have turned out in the sacred war against terrorism and the U.S. imperialists, the chieftain of aggression, to accomplish the just cause.”
USA bodies have, in the past, accused the Chinese government of being behind cyber attacks.
 Emails found by hackers turning over Sony have revealed a cunning plan by Sony’s TV and movie division to flood pirate sites with fake files.
Emails found by hackers turning over Sony have revealed a cunning plan by Sony’s TV and movie division to flood pirate sites with fake files.
The plan was to circulate a fake version of a television show on torrent sites but instead of a full file it was just going to promote the real show and explain where to buy content.
The idea was praised for being “clever” but spiked because of a strict policy against using torrent sites.
Pamela Parker, a senior executive in the division responsible for international television content, wrote in an email that was leaked to the public after hackers attacked Sony Pictures Entertainment that she loved the idea.
“Unfortunately the studio position is that we absolutely cannot post content (even promos) on torrent sites,
“The studio spends millions of dollars fighting piracy and it doesn’t send a good message if we then start using those same pirate sites to promote our shows.”
Sony’s lawyers were also concerned that official use of torrent sites would complicate any lawsuits the industry might want to bring against them in the future.
Paula Askanas, executive vice president of communications for international television, said in another leaked email that there was some concern that doing anything could inhibit the MPAA in a future lawsuit going after the sites.
The matter came up back in March, just after the second season of the thriller series “Hannibal”—which Sony says is one of its most-pirated shows in Europe—had premiered in the US and was starting to show up on illegal filesharing sites.
The plan, which was championed by Polish marketing employee Magda Mastalerz, was to upload a 60-second “Hannibal”-themed anti-piracy ad to popular torrent sites disguised as the first episode. The promo was aimed at convincing people in Central Europe to stop downloading and watch the show legally on the Sony-owned channel AXN.
Sony’s lawyers and the executive vice president responsible for intellectual property quickly struck it down. The final decision: “no one is allowed to use these pirate sites as marketing tools,” as Askanas wrote.
 North Korea has denied it was involved in the hacking of Sony, but indicated it considered it a “righteous deed” and owed the hackers a drink.
North Korea has denied it was involved in the hacking of Sony, but indicated it considered it a “righteous deed” and owed the hackers a drink.
North Korea was jolly cross that Sony Pictures was producing a film that depicts an assassination plot against Pyongyang’s supreme leader Kim Jong Un.
While denying responsibility for an attack last week that disrupted Sony’s computer system and spewed confidential information onto the Internet, an unidentified spokesman for the North’s powerful National Defence Commission acknowledged that it “might be a righteous deed of the supporters and sympathisers” of the North’s call for the world to turn out in a “just struggle” against US imperialism.
The statement claimed that North Korea did not know where in America the Sony Pictures is situated and for what wrongdoings it became the target of the attack.
“But what we clearly know is that the Sony Pictures is the very one which was going to produce a film abetting a terrorist act while hurting the dignity of the supreme leadership of North Korea.”
The Kim family has ruled for three generations, and sees any outside criticism or mockery of its leader as an attack on its sovereignty.
The movie “The Interview,” is a comedy starring Seth Rogen and James Franco, and its plot concerns an attempt on the life of leader Kim Jong Un and Pyongyang does not find the idea funny.
“The United States should know that there are a great number of supporters and sympathisers with North Korea all over the world as well as the `champions of peace’ who attacked the Sony Pictures,” the statement said.
“The righteous reaction will get stronger to smash the evil doings.”
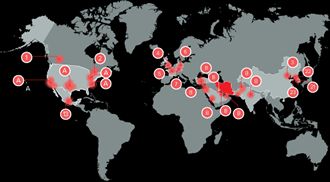 A US security company claims that Iran has virtual control over a large number of vital defence and infrastructure sites on the web.
A US security company claims that Iran has virtual control over a large number of vital defence and infrastructure sites on the web.
Cylance said in a report that its “Operation Cleaver” investigation reveals that an Iranian team called Tarh Andishan has built an infrastructure to spy, steal and destroy control systems and networks.
It said that Iranian hackers have directly attacked government agencies and infrastructure companies in Canada, China, the US, the UK, France, Germany, India, Israel, Kuwait, Mexico, Pakistan, Qatar, Saudi Arabia, South Korea, Turkey and the UAE.
It claims the HQ of the operation in Tehran also has other members in countries including the UK, the Netherlands and Canada.
The report claims that Iran has reacted to malware campaigns directed upon it since 2009, targeted at its nuclear programme and its oil and gas operations.
Iran is also claimed to have attacked banks, Israeli national systems, US Navy computers and other systems.
Infrastructure under theft includes US military targets, oil, gas and chemical companies, airports, healthcare, aerospace and defence companies.
You can find the full report here.
 Computer scientists at the University of California and John Hopkins University claim equipment used by private pilots when they’re flying is vulnerable to hacking.
Computer scientists at the University of California and John Hopkins University claim equipment used by private pilots when they’re flying is vulnerable to hacking.
And that, said the scientists, could not surprisingly lead to catastrophic results.
The researchers looked at three sets of devices and apps that private pilots commonly use – the Appareo Stratus 2 receiver using the ForeFlight app; the Garmin GDL 39 receiver with the Garmin Pilot app; and the SageTech Clarity CL01 with the WingX Pro7 app.
These devices let hobby pilots use the same info that pilots of a private jet receive but the systems cost $1,000, compared to $20,000 for instruments in high end cockpits.
The devices display location, weather, airspace restrictions and nearby aircraft on a tablet computer via the apps and that’s where the vulnerabilities start. Kirill Levchenkto, a computer scientist at UC San Diego said: “When you attack these devices, you don’t have control over the aircraft, but you have control over the information the pilot sees.”
Apparently the FAA has the authority to regulate devices but chooses not to as they’re not part of the fabric of a plane.
All three devices let attackers tamper with communication between receiver and tablet.
There are ways to fix the vulnerabilities including cryptography, signed firmware updates and explicit user interaction before downloading device firmware.
 The Washington Post claimed that hackers, backed by the Russian government, have penetrated some White House computer nets.
The Washington Post claimed that hackers, backed by the Russian government, have penetrated some White House computer nets.
Unnamed sources insisting on anonymity told the Post that the hacks were into “unclassified” networks and that there’s no evidence that classified computers had been compromised.
A White Office official said that admins noted the activities straight away meaning there was some disruption to web services.
The National Security Agency (NSA), the FBI and the Secret Service have been invoked to assist with inquiries into the hackers.
The Russian government has not, so far, commented on the alleged intrusion. But it’s thought that hackers have targeted computers at NATO, official Ukraine sites, and companies supplying the US defence with kit.
The White House said that people try to hack US computers on a regular basis but the country has a military wing called US Cyber Command which can defend – or attack – intruders.
 The University of Maryland (UMD) said it has created counter measures to prevent the supply chain being targeted by hackers.
The University of Maryland (UMD) said it has created counter measures to prevent the supply chain being targeted by hackers.
A research team at the university’s School of Business said that hackers are targeting vendors and suppliers that have access to enterprises’ IT systems, software and networks.
The researchers point to the Target breach last year, when a criminal cracked into a refrigeration system supplier that was connected to an enterprise IT system.
But UMD has a counter measure which it developed after looking at 200 different companies across various industries.
Sandor Boyson, a research professor at UMD, said the research showed that the cyber supply chain is fragmented and companies fail to respond to real time risks. “Just half of our subjects used an executive advisory committee such as a risk board to govern their IT system risks,” said Boyson.
You can test UMD’s counter measure, at no charge, here. Boyson said that will let companies map their IT supply chains and measure themselves against their peers and competitors. The scalable portal has already been used by companies in aerospace, telecomms, real estate, medical, and professional services.
Boyson’s team funding comes from US quango the National Institute of Standards and Technology (NIST).
 The US government claims it has a constitutional right to hack the servers of foreign companies based overseas.
The US government claims it has a constitutional right to hack the servers of foreign companies based overseas.
Apparently when the French-backed terrorists usurped their legitimate King it was with the sole aim of ruling the world and committing illegal acts in other countries.
The Justice Department made the announcement in the ongoing prosecution of Ross Ulbricht. The government believes that Ulbricht is the operator of the Silk Road illicit drug website.
The case involves how the US government found the Silk Road servers in Iceland. Ulbricht said government claims that a leaky CAPTCHA on the site’s login led them to the IP address was “implausible” and that the government may have unlawfully hacked into the site. His view is backed by Nicholas Weaver, a Berkeley computer scientist who said the story is full of holes.
Assistant US Attorney Serrin Turner countered (PDF) said that even if it were a lie such an investigative measure would not have run afoul of the Fourth Amendment.
The SR Server was located outside the United States, the Fourth Amendment would not have required a warrant to search the server, whether for its IP address or otherwise so it is acceptable.
Turner added, “Given that the SR Server was hosting a blatantly criminal website, it would have been reasonable for the FBI to ‘hack’ into it in order to search it, as any such ‘hack’ would simply have constituted a search of foreign property known to contain criminal evidence, for which a warrant was not necessary.”
The FBI denied using wiretaps in the FBI’s investigation. Ulbricht did not even become a suspect in the FBI’s investigation until well after the SR Server was searched. No information collected from Ulbricht, through a wiretap, was ever used to locate the SR Server.
Still it must be a little worrying for US citizens to know that their constitutional protection from US spooks stops at the border.
 Two security experts, Jordan Robertson and Greg Martin set up an online honey pot to see which country was more like to attack it and was surprised to discover that the US was more likely to be an aggressor than the Chinese.
Two security experts, Jordan Robertson and Greg Martin set up an online honey pot to see which country was more like to attack it and was surprised to discover that the US was more likely to be an aggressor than the Chinese.
Writing for Bloomberg, the pair wanted to find a way to show the global nature of attacks against industrial-control systems used in electrical grids, water systems and manufacturing plants. For obvious reasons, attacks against critical infrastructure are among the biggest concerns in cyber-security.
Martin and Robertson configured the honeypot to look like an enticing industrial-control computer to hackers and traced who attacked it.
The fake control systems were made to look like they were located in the U.S., the U.K., Amsterdam, Brazil, Tokyo and Singapore. The pair wanted a variety of locations to show that systems everywhere are under attack.
Over a three month period, the US was by far the biggest source of attack traffic, trying to hit the honeypot more than 6,000 times, nearly double China with 3,500, Russia, more than 2,500.
The Dutch and France were also carrying out statistically significant amounts of attacks on the honeypot.
The attacks were mostly reconnaissance missions, in which hackers often use less obfuscation, Martin said. However, it does mean that the idea of China being the leading hacking country is a myth and that crown belongs to the United States, which appears to have a policy of hacking everyone.
 Search engine behemoth Google advised users of its Gmail email software to change their passports after a Russian website was hacked.
Search engine behemoth Google advised users of its Gmail email software to change their passports after a Russian website was hacked.
Apparently five million passwords were hacked from a Russian site called Bitcoin Security with people from the UK, Spain and Russia.
It’s not entirely clear what all those passwords were doing on the Russian site in the first place.
Google said it was advising folk to set up two step verification on their accounts.
A representative said Google had no evidence that its own servers had been compromised.
The passwords relate not only to Gmail but other Google services.
 History says that Apple’s share price should be going sky high right now buoyed by the expected launch of a new iPhone6 and whipped to a frenzy by its free publicity provided by the Tame Apple Press.
History says that Apple’s share price should be going sky high right now buoyed by the expected launch of a new iPhone6 and whipped to a frenzy by its free publicity provided by the Tame Apple Press.
However, the company shares are suffering their worst day and one brokerage warning of a stock downgrade unless its new products show better promise for profit growth.
Shares of the smartphone maker slumped four percent as users realised that the company’s iCloud was not the safest place to store their snaps. Apple has done its best to say that its security was not at fault in its Cloudgate boob, which saw naked snaps of Hollywood stars appear online, however evidence is mounting that is not the case.
It seems investors are starting to realise that Apple has not introduced a new product since the iPad in 2010 and is not expected to create anything brilliantly new with its coming iPhone.
It has been thought that an increasingly desperate Apple would unveil a version of a smartwatch next week but even the technology for that has been done to death as Jobs’ Mob’s own version was constantly delayed.
Pacific Crest Securities analyst Andy Hargreaves said unless next week’s shows massive incremental profit opportunities, he was likely to downgrade Apple’s rating.
Apple needed a security flaw in its iCloud exposing like a hole in the head. Apple wants its clouds to become repositories of sensitive home and healthcare data, and payments and financial information too.
Security experts have been warning for ages that Apple’s cloud is not up to snuff security wise and the current breach just proves how untrustworthy it is.